TLS certificates are automatically applied to the preview URLs and custom domains of services deployed with ale.
Cert Generator Install & Issue
Set the values used in the certificate generation script as environment variables.
export AWS_REGION =< AWS Region > export AWS_DOMAIN =< Route53 Domain > export AWS_HOSTED_ZONE_ID =< Route53 Hosted Zone ID > export ACME_EMAIL =< Certificate Issuance Email >
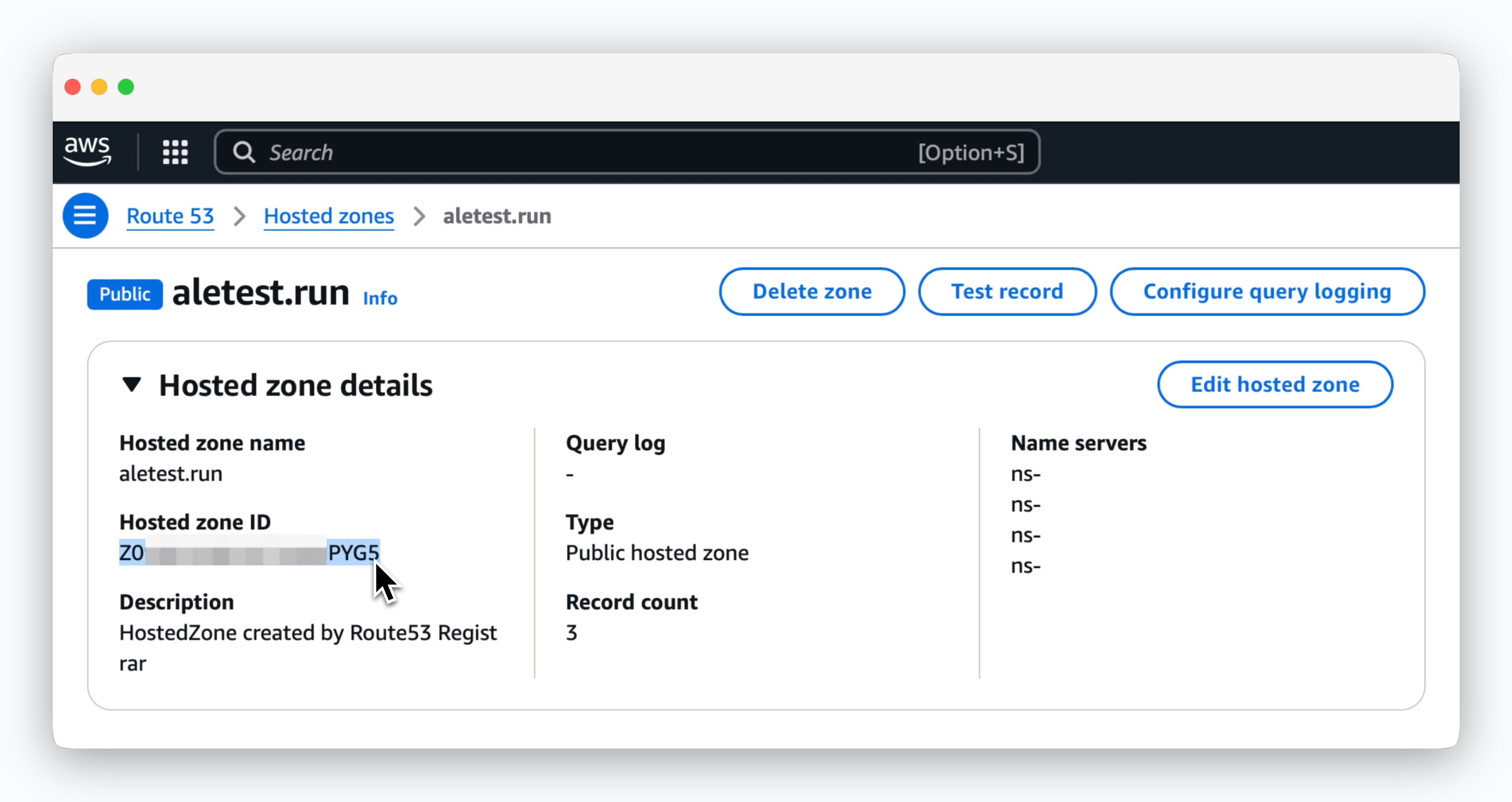
AWS Route53 Hosted Zone ID
You can find the Hosted Zone ID in Route53 > Hosted Zones > Hosted Zone Details .
Install the cluster certificate generator using the following command.
cat << EOF | kubectl apply -f - apiVersion: v1 kind: Secret metadata: name: aws-secret-access-key namespace: cert-manager type: Opaque stringData: aws-secret-access-key: $AWS_SECRET_ACCESS_KEY --- apiVersion: cert-manager.io/v1 kind: ClusterIssuer metadata: name: ale-issuer namespace: cert-manager spec: acme: email: $ACME_EMAIL server: https://acme-v02.api.letsencrypt.org/directory privateKeySecretRef: name: ale-issuer solvers: - http01: ingress: class: nginx - dns01: route53: region: $AWS_REGION hostedZoneID: $AWS_HOSTED_ZONE_ID accessKeyID: $AWS_ACCESS_KEY_ID secretAccessKeySecretRef: name: aws-secret-access-key key: aws-secret-access-key selector: dnsZones: - $AWS_DOMAIN EOF
Run the following command to issue a certificate.
cat << EOF | kubectl apply -f - apiVersion: cert-manager.io/v1 kind: Certificate metadata: name: ale-app-tls namespace: cert-manager spec: dnsNames: - "*. $AWS_DOMAIN " issuerRef: kind: ClusterIssuer name: ale-issuer secretName: ale-app-tls EOF
Ingress Setup
Create an Ingress to access ale using the following command.
cat << EOF | kubectl apply -f - apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: ale namespace: ale annotations: nginx.ingress.kubernetes.io/whitelist-source-range: 0.0.0.0/0 cert-manager.io/cluster-issuer: ale-issuer spec: ingressClassName: nginx tls: - hosts: - app. $AWS_DOMAIN secretName: ale-controller-tls rules: - host: app. $AWS_DOMAIN http: paths: - path: / pathType: Prefix backend: service: name: ale-controller port: number: 9001 EOF
Use the following command to verify that the certificates have been created and applied. If created successfully, the STATE field should show as valid.
kubectl get order -n ale \ | awk '/ale-/{print $1}' \ | xargs kubectl get order -n ale
NAME STATE AGE ale-controller-tls-1-1997619857 valid 103s
If you can access the following URLs, the certificate has been applied successfully. If access fails, check the status of the Cert Manager pod or the Cluster Issuer.
https://app.[Route53_Domain]
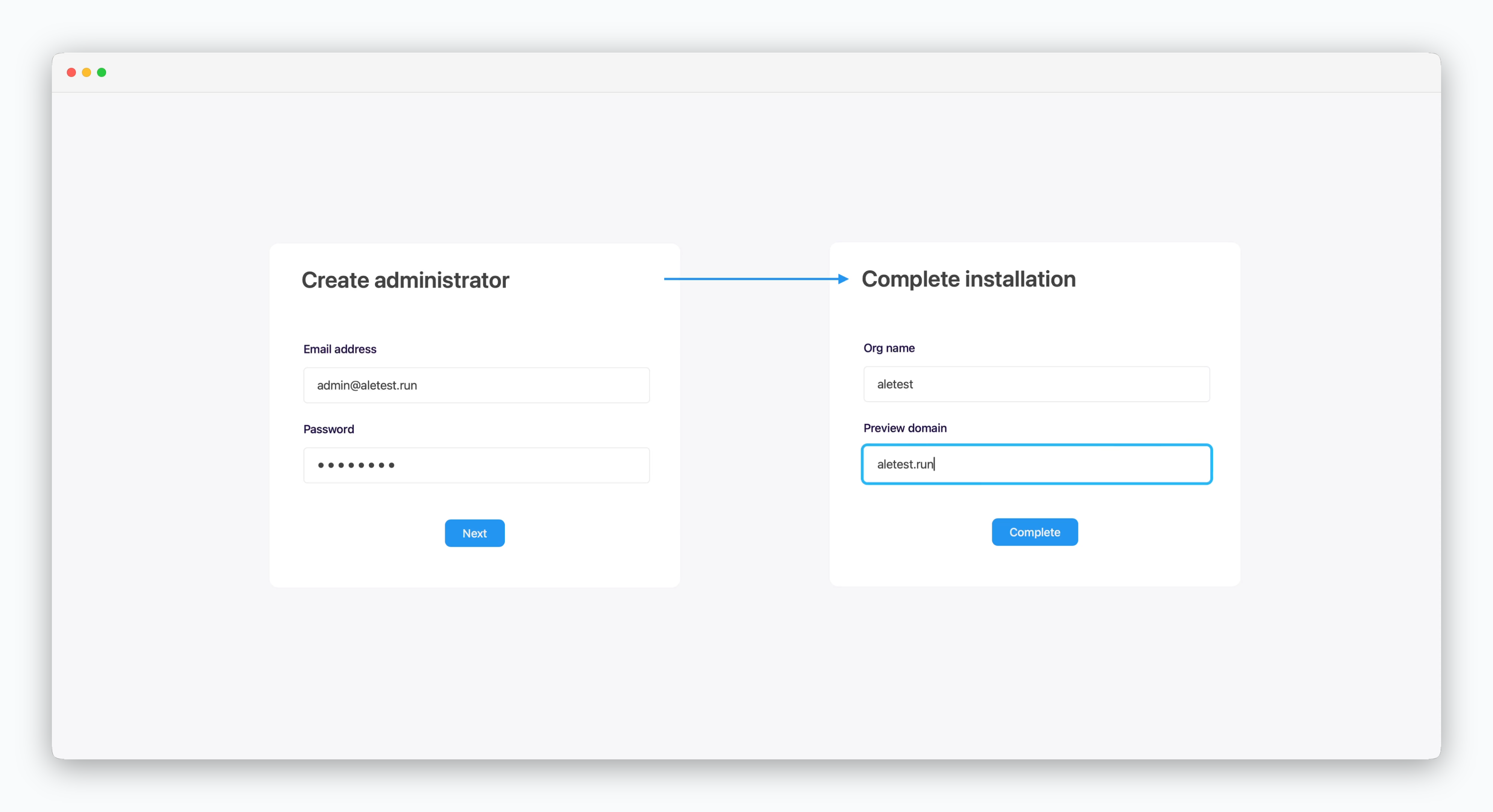
Create an administrator account and complete the installation.
Enter the root domain in the preview domain field.
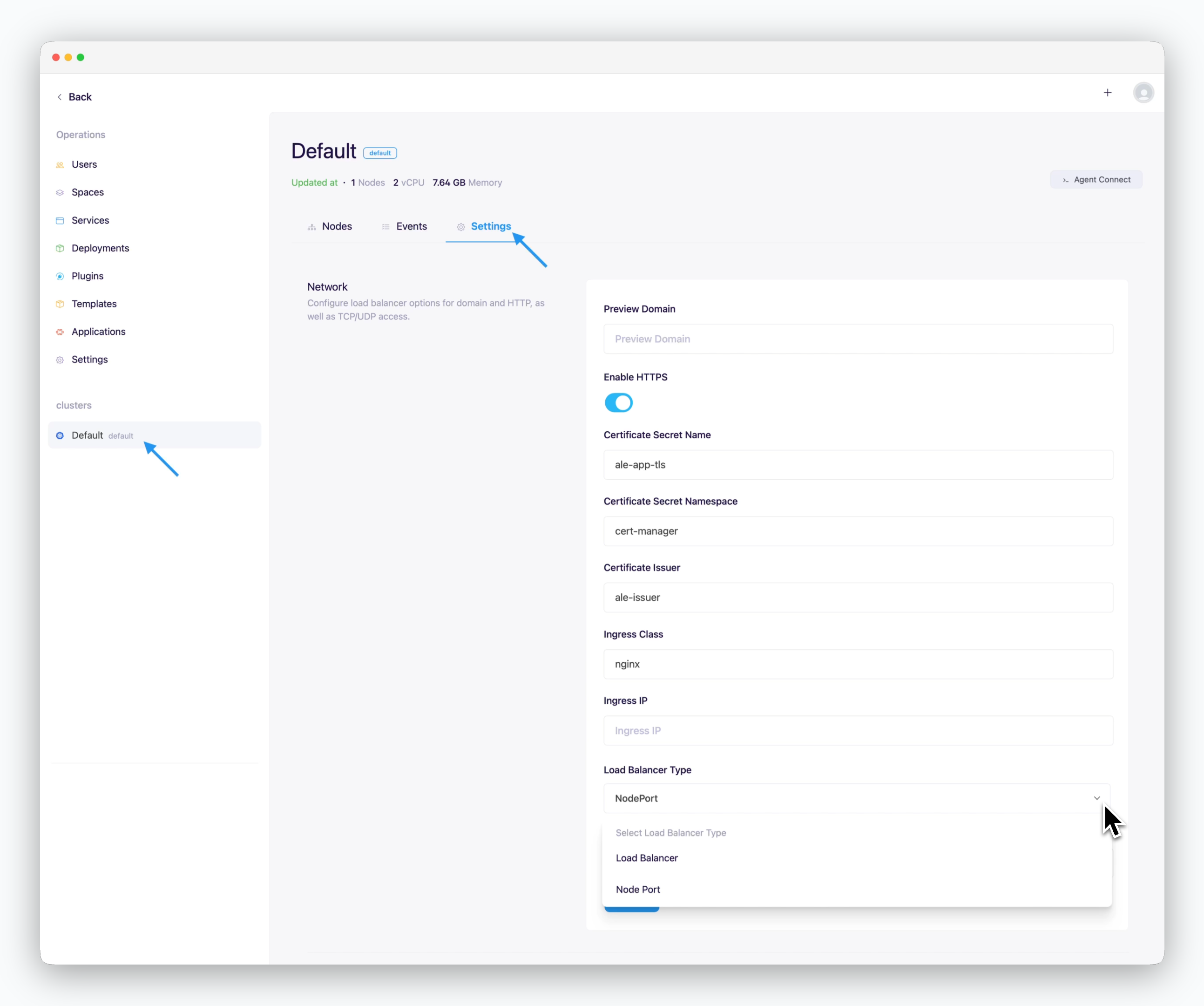
Cluster Network Configuration
On the cluster page in the Operations System, navigate to the Settings tab and enter the following values in the Network section.
Preview Domain : Root domain of Route53Use HTTPS
Checked : Internet environmentUnchecked : Intranet/closed network environment
Certificate Secret Name : ale-app-tlsCertificate Secret Namespace : cert-managerCertificate Issuer : ale-issuerIngress Class : nginxIngress IP : Blank (Auto-detected)Load Balancer Type
Ingress/Egress Bandwidth : Enter in Mbps
You can access the operations system by clicking the space name in the dashboard. The operations system menu is only displayed for accounts with access permissions to the operations system.