Create DNS Record for preview URL
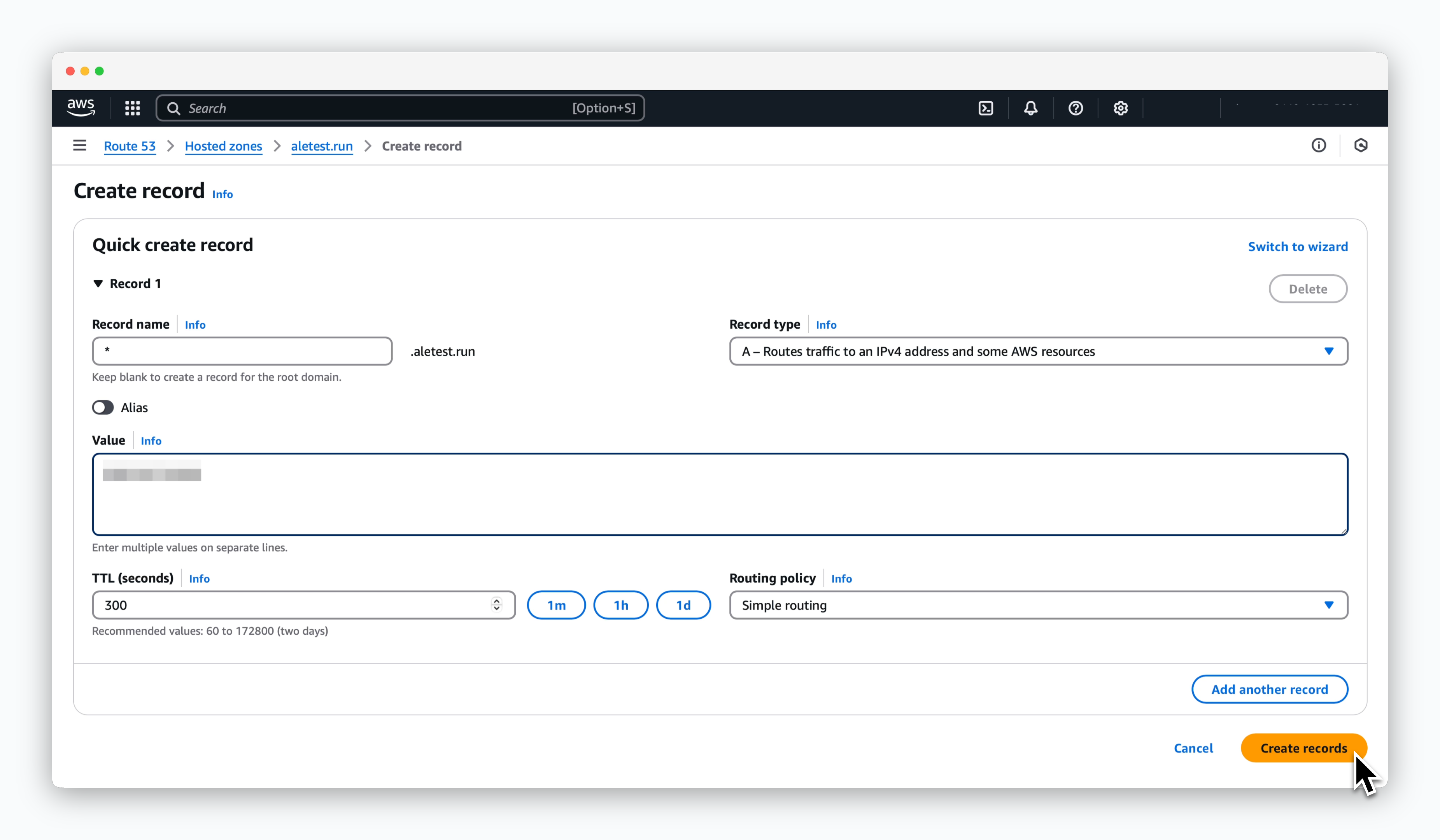
Click Create record on the target domain page in the Route53 dashboard and create a record with the following values:
- Record name: *
- Record type: A
- Value: Public IP address of EC2 instance
Through this process, the root domain with the registered record is assigned as a preview URL for the service deployed on the dashboard.
You can verify if the record has been propagated to the nameserver using the following command:
Install Cert Manager
Run the following commands to install Cert Manager:
ClusterIssuer & TLS Certificates
Use the following command to create the ClusterIssuer and TLS certificate:
Setup Ingress in ale
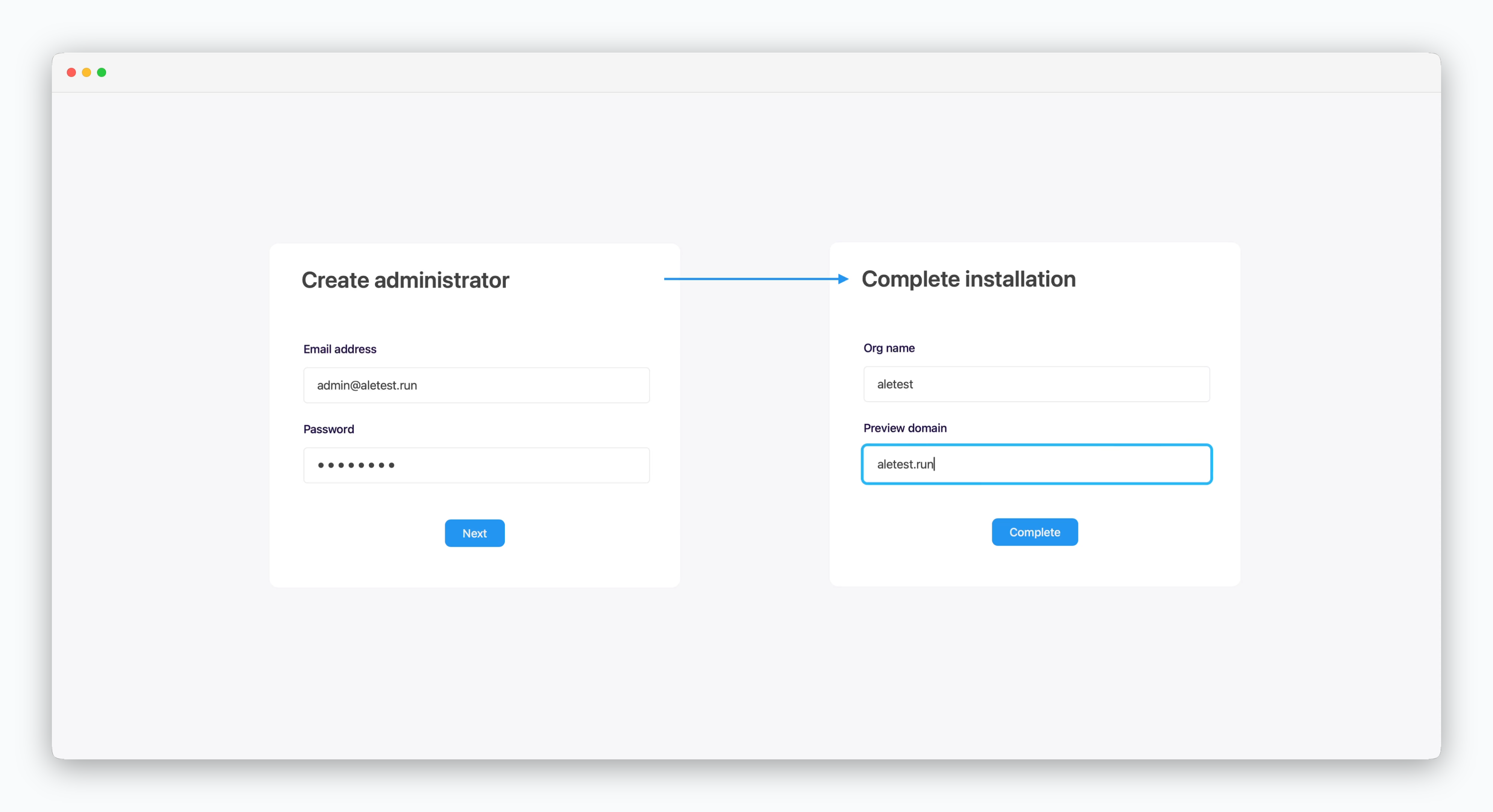
Accessaleathttps://app.[domain], create an administrator, and complete the installation.
Enter the root domain in the preview domain field.
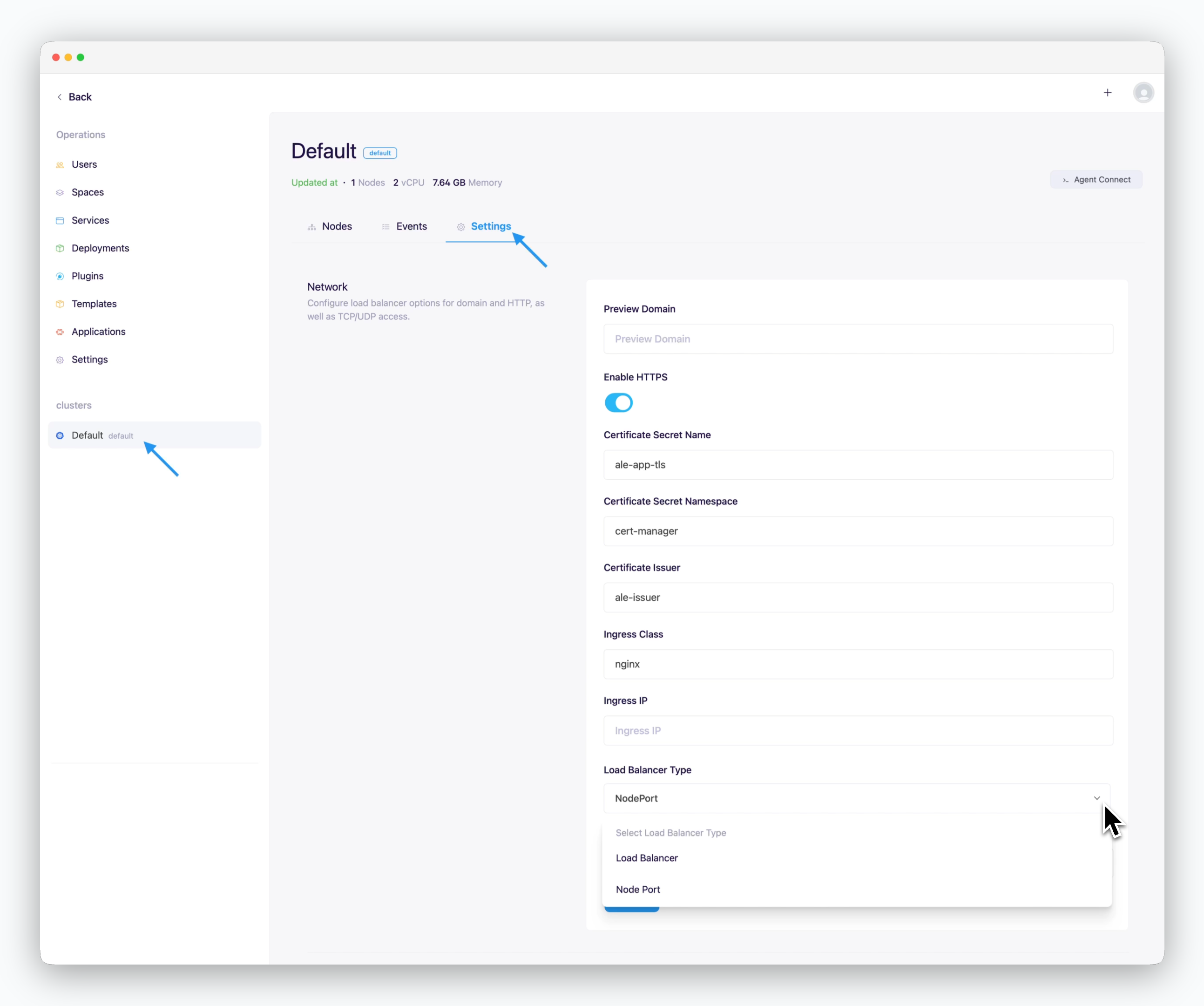
Enter the following values in the network section of the settings tab in the cluster page and click Apply.
- Preview domain: Connected root domain
- Use HTTPS
- Activate: Internet environment
- Inactivate: Intranet/closed network environment
- Certificate secret name: ale-app-tls
- Certificate secret namespace: cert-manager
- Certificate issuer: ale-issuer
- Ingress class: nginx
- Load balancer type: NodePort
You can access the operations system by clicking the space name in the dashboard.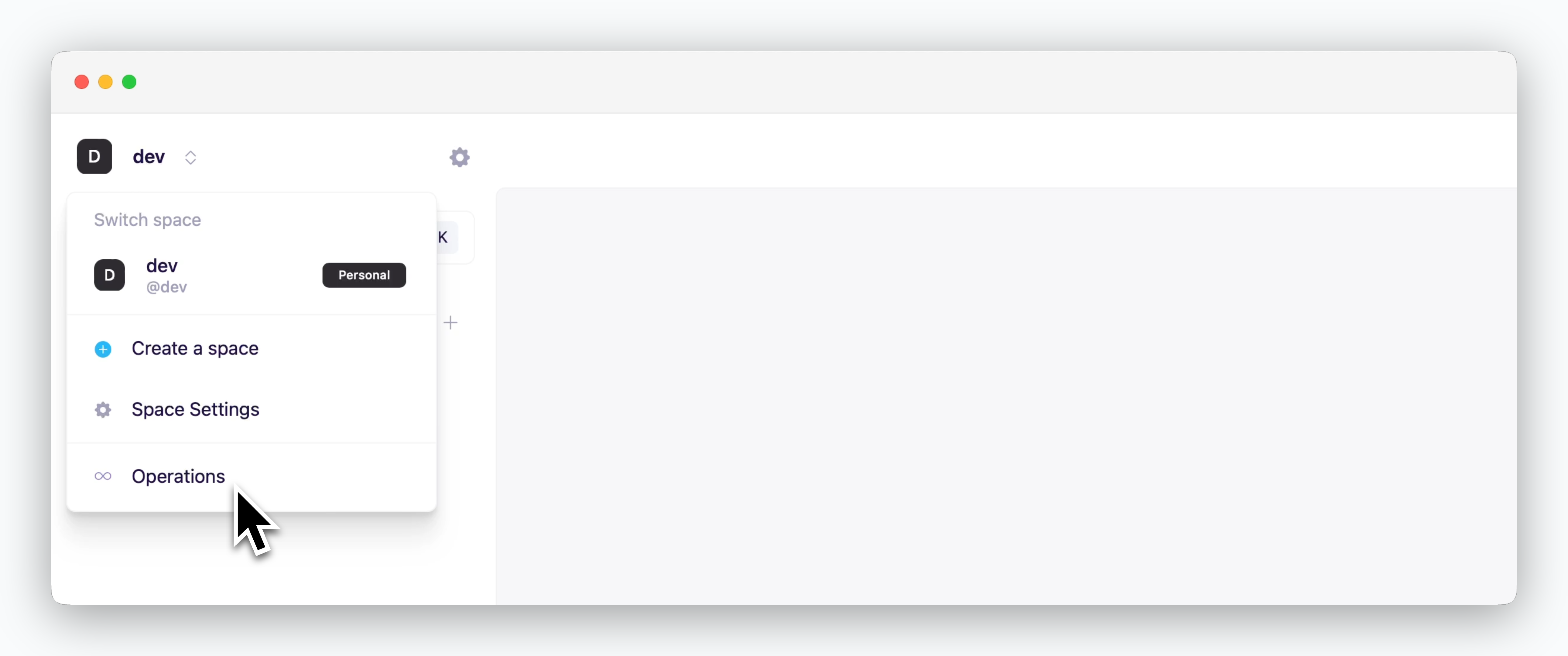

The operations system menu is only displayed for accounts with access permissions to the operations system.
Access ale Dashboard
ClickBackin the top left of the operations system or accessaleathttps://app.[domain]and complete the signup process to use the developer dashboard.
Refer to the cards below for instructions on using the operations system and developer dashboard.